How To Add 2019 Dc To 2008r2 Domain
Today I want to share with yous a direct feel from the field.
One customer received a request from their security team to disable the RC4 ETYPE (Encryption Type) for Kerberos for their Windows ten Clients. The support team created a GPO to disable this Etype without thinking besides much about the consequences.
ENVIRONMENT

The customer take all DCs with Windows Server 2008R2 and the DFL (Domain Functional Level) and the FFL (Wood Functional Level) are set to 2008R2. All Clients are Windows ten CB (Current Branch) Build 1803.
THE PROBLEM
The support squad created a GPO to disable the RC4 Etype on Windows 10 Clients by using this GPO:
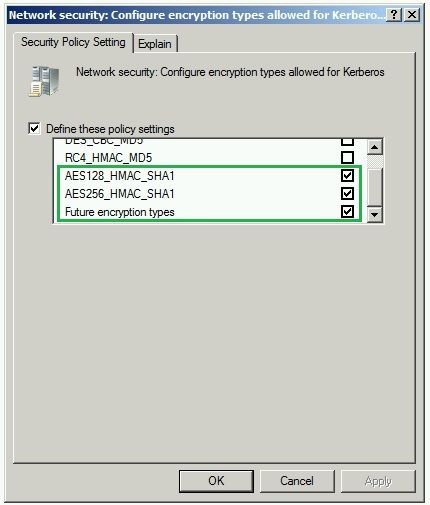
The GPO was practical in the It.CONTOSO.COM domain on the OU of the Windows ten Clients:
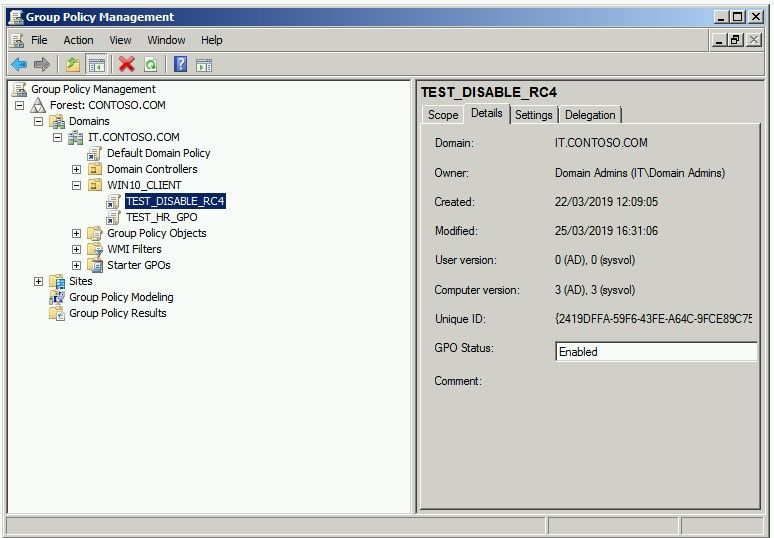
Afterwards that, the team responsible of the clients commencement opening tickets regarding the impossibility of some windows ten clients to utilise the GPOs, then we was involved for the troubleshooting.
TROUBLESHOOTING
In ane of the affected windows x clients we noticed this effect:
================================================
Log Name: System
Source: Microsoft-Windows-GroupPolicy
Date: three/28/2019 11:09:25 AM
Event ID: 1006
Task Category: None
Level: Fault
Keywords:
User: System
Computer: CLIENT01.IT.CONTOSO.COM
Description:
The processing of Grouping Policy failed. Windows could not authenticate to the Active Directory service on a domain controller. (LDAP Bind role phone call failed). Look in the details tab for error code and description.
================================================
So we have enabled on the Windows 10 Customer the Grouping Policy Debug Logging from regedit:

By executing on the client a GPUPDATE /FORCE we received the following fault message:

And in the debug log ( %windir%\debug\usermode\gpsvc.log ) of the Grouping Policy Service, we found the following error message:
********************************
GPSVC(1478.1d08) xi:25:22:416 SearchDSObject: Searching <OU=WIN10_CLIENT,DC=It,DC=CONTOSO,DC=COM>
…….
GPSVC(1478.1d08) 11:25:22:433 EvaluateDeferredGPOs: Doing an ldap demark to cantankerous-domain <60 minutes.CONTOSO.COM>
GPSVC(1478.1d08) 11:25:22:448 EvaluateDeferredGPOs: ldap_bind_s failed with = <82>
GPSVC(1478.1d08) 11:25:22:448 GetGPOInfo: EvaluateDeferredGPOs failed. Exiting
GPSVC(1478.1d08) eleven:25:22:448 GetGPOInfo: Leaving with 0
********************************
This kind of fault testify usa that the client is trying to practise an LDAP binding the other child Domain Hr.CONTOSO.COMsimply why? The customer is joined to the Information technology.CONTOSO.COM Domain!!
So nosotros verified all the GPO practical to the Windows 10 clients from the GPMC (Group Policy Direction Console) , by looking at the GPO inheritance of the OU, and we found that a GPO from HR.CONTOSO.COM was applied to the clients in IT.CONTOSO.COM:

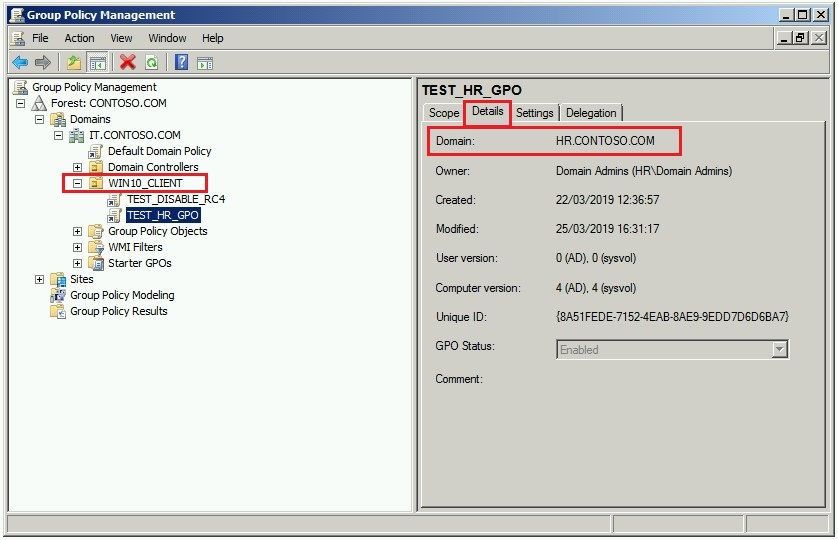
Every bit yous tin run into this is my lab, and information technology is easy to discover the GPO :) , but in a real production environment you demand to bank check the details tab on all the GPO applied in the inheritance tab of the Windows x Clients OU.
Now we know why the client try to accomplish the HR.CONTOSO.COM Domain during the application of the GPOs, merely why is not able to authenticate?
Then we verified the eventlog on the DCs and we establish this mistake bulletin:
=====================================
Log Name: System
Source: Microsoft-Windows-Kerberos-Central-Distribution-Middle
Date: iii/29/2019 five:17:26 PM
Result ID: 14
Task Category: None
Level: Fault
Keywords: Classic
User: N/A
Description:
While processing an AS asking for target service krbtgt, the business relationship Administrator did not accept a suitable key for generating a Kerberos ticket (the missing key has an ID of ane). The requested etypes : 18 17 3. The accounts bachelor etypes : 23 -133 -128. Irresolute or resetting the password of Administrator will generate a proper fundamental.
=====================================
This event show us that we take an outcome related to the ETYPE for Kerberos.
RESOLUTION
If the Windows x clients need to cosign in the other child domain (HR.CONTOSO.COM), demand to use the default Parent-Kid trusts, but this trusts by default uses RC4 as ETYPE for Kerberos.
So if you want to enable AES on this trusts you lot need to enable this flag (disabled past default) in the trusts properties:
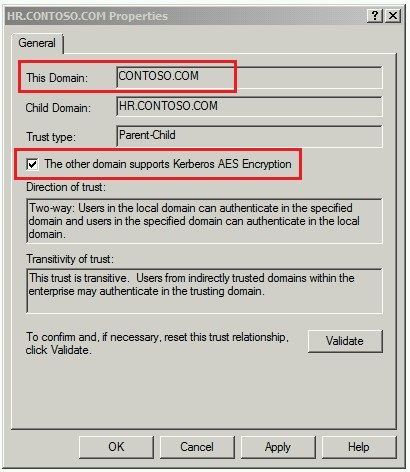
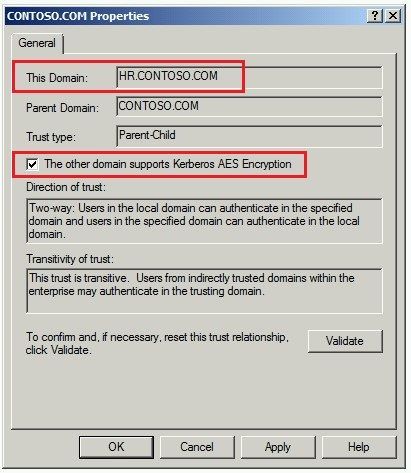
Because the Parent-Child trust is a Two-way transitive you need to enable this flag on the parent (CONTOSO.COM) and on the child'due south domains (Information technology & HR.CONTOSO.COM).
TO Continue IN MIND
If you lot set this flag in the trusts Properties:

You lot are enabling only AES 128 and AES 256 on the Trust, the RC4 will be Disabled
If you want to configure the trust to back up RC4,AES 128 and AES258, you need to use the KSETUP command line utility.
In this case I'm continued to the CONTOSO.COM DC and from a command line I will enable the selected Etypes on the trust for IT.CONTOSO.COM:
========================================================
ksetup /setenctypeattr information technology.contoso.com RC4-HMAC-MD5 AES128-CTS-HMAC-SHA1-96 AES256-CTS-HMAC-SHA1-96
========================================================
If you want to verify if you accept done a proficient chore with the KSETUP, you can use the ADSIEdit,and verify the msDS-SupportedEncryptionTypesaspect of the Trust if it is set to 0x1C:


THE FINAL Respond
At the terminate, can I disable the RC4 as an ETYPE for Kerberos on my Windows 10 Clients?
If you have all your DCs at least 2008R2 with DFL and FFL 2008R2, Yes you can, just remember:
- Test e'er the new configuration of ETYPE in Pre-Production environment first!
- Remember to Enable the AES ETYPE on the Trusts.
- If all the tests in Pre-Product gone well, then you can start to apply the GPO on a pocket-size fix of friendly Clients, and set up e'er a rollback plan.
- Examination all your core concern Applications on this small prepare of clients.
- Utilize the GPO to an increasing number of groups of clients but ever step by step.

How To Add 2019 Dc To 2008r2 Domain,
Source: https://techcommunity.microsoft.com/t5/itops-talk-blog/tough-questions-answered-can-i-disable-rc4-etype-for-kerberos-on/ba-p/382718
Posted by: arringtonungazintonat.blogspot.com


0 Response to "How To Add 2019 Dc To 2008r2 Domain"
Post a Comment